Wireshark Monitor Results
[Test 1]
h4
| | |
h1 h2 h3
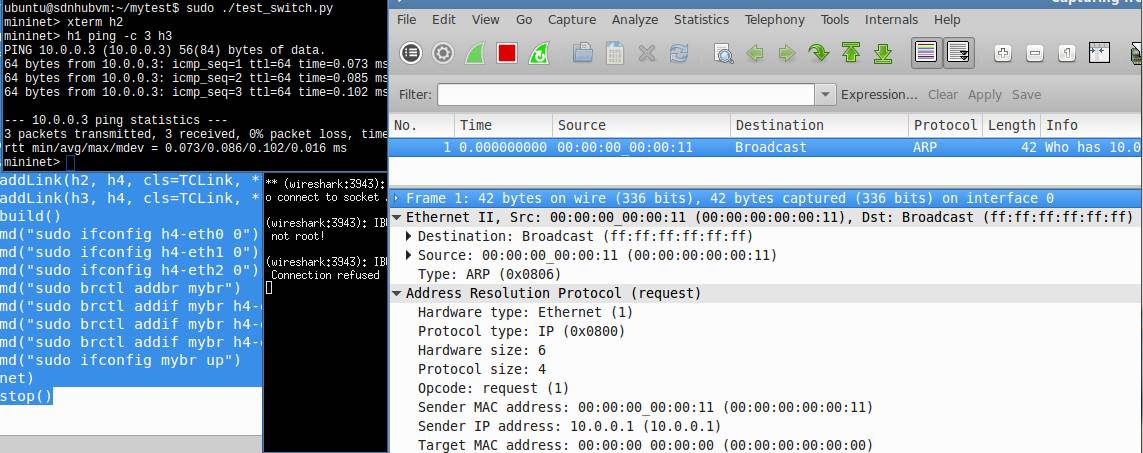
h1,h2,h3 are hosts. h4 will be configured as a switch. We will monitor the ping packets transmitted between h1 and h3 at host h2. Due to the mac address learning feature, we can see the arp request packet sent by h1 using broadcast at host h2. Then we can see nothing at h2. Because the switch will direct forward the packets to/from h1 and h3 directly.
mininet-script
|
#!/usr/bin/env python from mininet.cli import CLI from mininet.link import Link,TCLink,Intf from mininet.net import Mininet from mininet.node import RemoteController from mininet.term import makeTerm
if '__main__' == __name__: net = Mininet(link=TCLink) h1 = net.addHost('h1', mac='00:00:00:00:00:11') h2 = net.addHost('h2', mac='00:00:00:00:00:22') h3 = net.addHost('h3', mac='00:00:00:00:00:33') h4 = net.addHost('h4', mac='00:00:00:00:00:44') linkopts={'bw':1} net.addLink(h1, h4, cls=TCLink, **linkopts) net.addLink(h2, h4, cls=TCLink, **linkopts) net.addLink(h3, h4, cls=TCLink, **linkopts) net.build() h4.cmd("sudo ifconfig h4-eth0 0") h4.cmd("sudo ifconfig h4-eth1 0") h4.cmd("sudo ifconfig h4-eth2 0") h4.cmd("sudo brctl addbr mybr") h4.cmd("sudo brctl addif mybr h4-eth0") h4.cmd("sudo brctl addif mybr h4-eth1") h4.cmd("sudo brctl addif mybr h4-eth2") h4.cmd("sudo ifconfig mybr up") CLI(net) net.stop() |
execution
[Test 2]
h6
|
h5
|
h1,h2,h3,h4
h1, h2,h3,h4 are hosts, h5 is a switch, and h6 is a
router.
h1 and h2 are in the same VLAN while h3 and h4 are in the
same vlan.
mininet-script
|
#!/usr/bin/env python from mininet.cli import CLI from mininet.link import Link,TCLink,Intf from mininet.net import Mininet from mininet.node import RemoteController if '__main__' == __name__: net = Mininet(link=TCLink) h1 = net.addHost('h1') h2 = net.addHost('h2') h3 = net.addHost('h3') h4 = net.addHost('h4') #h5 is a
switch h5 = net.addHost('h5') #h6 is a
switch h6 = net.addHost('h6') Link(h1,
h5) Link(h2,
h5) Link(h3,
h5) Link(h4,
h5) Link(h5,
h6) net.build()
h1.cmd("ifconfig h1-eth0 0")
h2.cmd("ifconfig h2-eth0 0")
h3.cmd("ifconfig h3-eth0 0")
h4.cmd("ifconfig h4-eth0 0")
h5.cmd("ifconfig h5-eth0 0")
h5.cmd("ifconfig h5-eth1 0")
h5.cmd("ifconfig h5-eth2 0")
h5.cmd("ifconfig h5-eth3 0") h5.cmd("ifconfig h5-eth4 0")
h6.cmd("ifconfig h6-eth0 0")
h5.cmd("vconfig add h5-eth4 10")
h5.cmd("vconfig add h5-eth4 20")
h6.cmd("vconfig add h6-eth0 10")
h6.cmd("vconfig add h6-eth0 20")
h5.cmd("ifconfig h5-eth4.10 up")
h5.cmd("ifconfig h5-eth4.20 up")
h5.cmd("brctl addbr
brvlan10")
h5.cmd("brctl addbr
brvlan20")
h5.cmd("brctl addif
brvlan10 h5-eth0")
h5.cmd("brctl addif
brvlan10 h5-eth1")
h5.cmd("brctl addif
brvlan10 h5-eth4.10")
h5.cmd("brctl addif
brvlan20 h5-eth2")
h5.cmd("brctl addif
brvlan20 h5-eth3")
h5.cmd("brctl addif
brvlan20 h5-eth4.20")
h5.cmd("ifconfig brvlan10 up")
h5.cmd("ifconfig brvlan20 up")
h6.cmd("echo 1 > /proc/sys/net/ipv4/ip_forward")
h6.cmd("ifconfig h6-eth0.10 10.0.10.254
netmask 255.255.255.0")
h6.cmd("ifconfig h6-eth0.20 10.0.20.254
netmask 255.255.255.0")
h1.cmd("ifconfig h1-eth0 10.0.10.1 netmask 255.255.255.0")
h2.cmd("ifconfig h2-eth0 10.0.10.2 netmask 255.255.255.0") h3.cmd("ifconfig h3-eth0 10.0.20.1 netmask
255.255.255.0")
h4.cmd("ifconfig h4-eth0 10.0.20.2 netmask 255.255.255.0")
h1.cmd("ip route add default via
10.0.10.254 dev h1-eth0")
h2.cmd("ip route add default via
10.0.10.254 dev h2-eth0")
h3.cmd("ip route add default via
10.0.20.254 dev h3-eth0")
h4.cmd("ip route add default via
10.0.20.254 dev h4-eth0")
h1.cmd("tcpdump -i
h1-eth0 -U -w h1.log &")
h4.cmd("tcpdump -i
h4-eth0 -U -w h4.log &")
h6.cmd("tcpdump -i
any -U -w h6.log &")
h1.cmd("ping -c 3 10.0.20.2") CLI(net) net.stop() |
execution
![]()
after execution, use wireshark
to see the results.
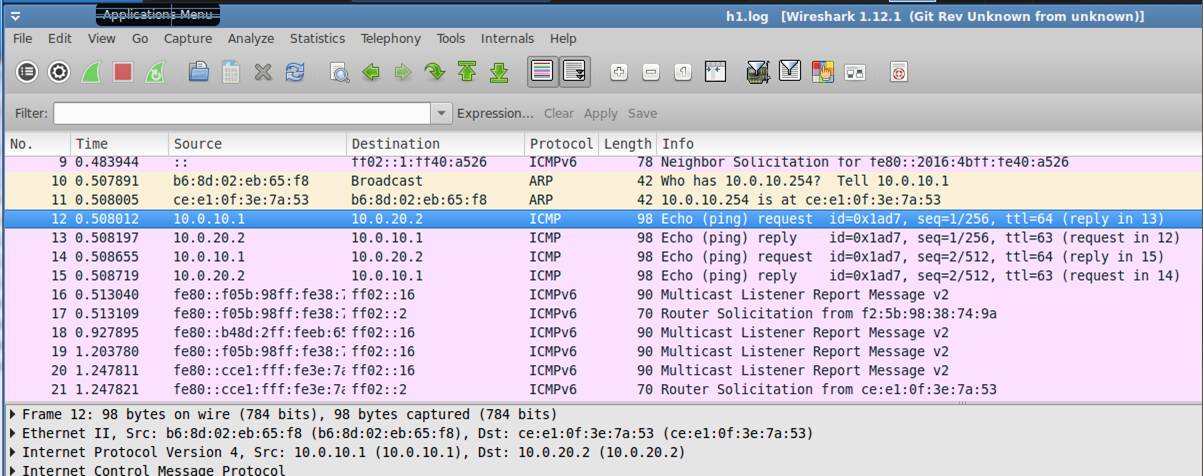
h1.log: Normal Ethernet II Mac Header (No tagging)
![]()
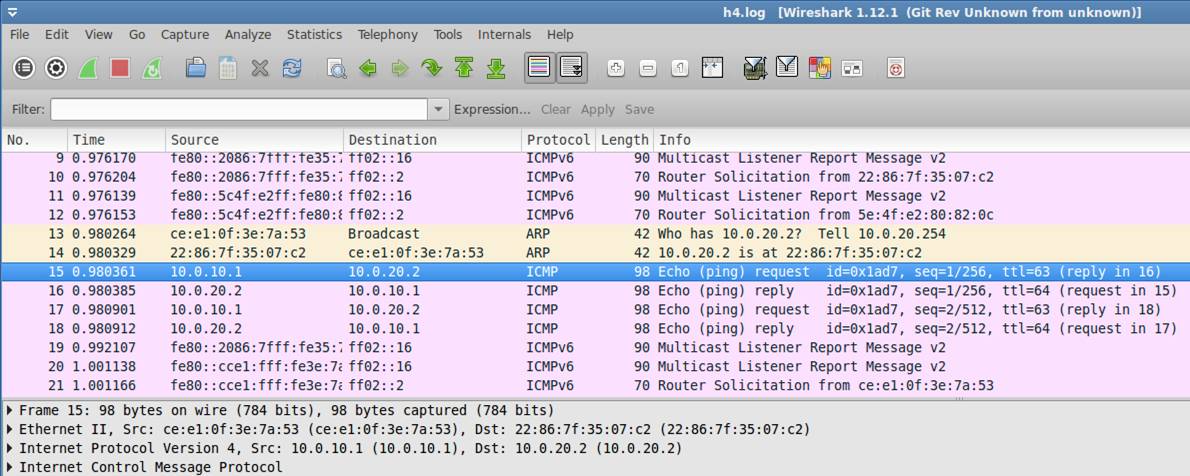
h4.log: Normal Ethernet II Mac Header (No tagging)
![]()
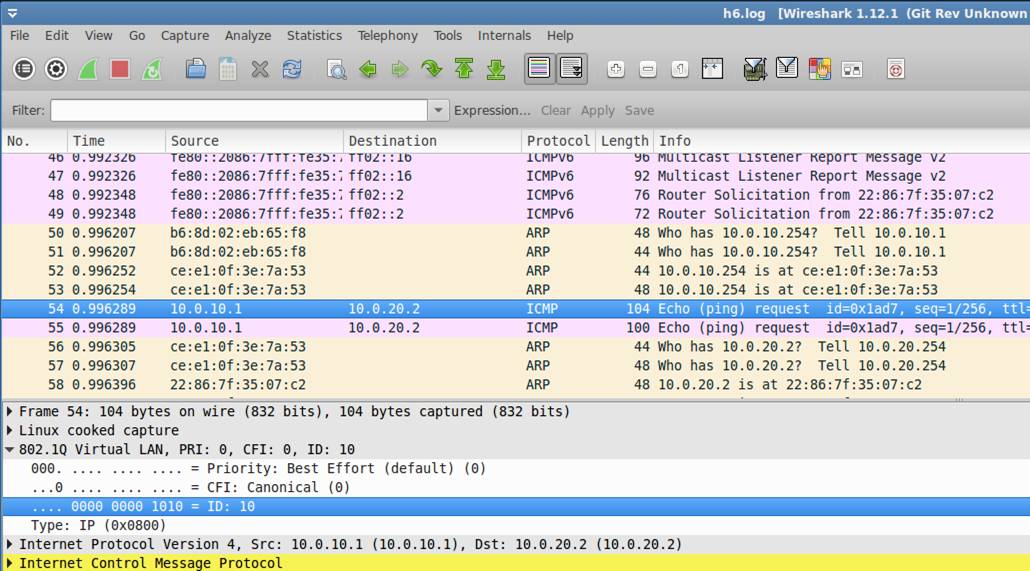
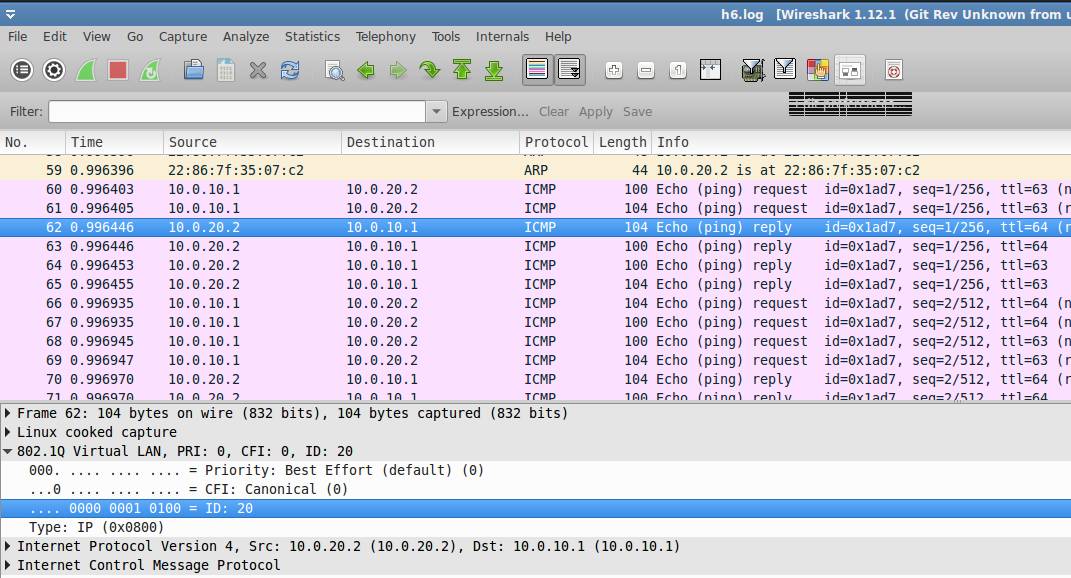
h6.log: You can see 802.1Q header (Tagging)
![]()
(when h1 sends the ICMP packets to h4, we can see the
VLAN ID =10)
(when h4 sends the ICMP packets to h1 we can see the VLAN
ID =20)
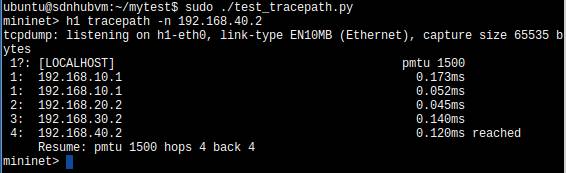
[Test 3]
h1---h2---h3--h4---h5
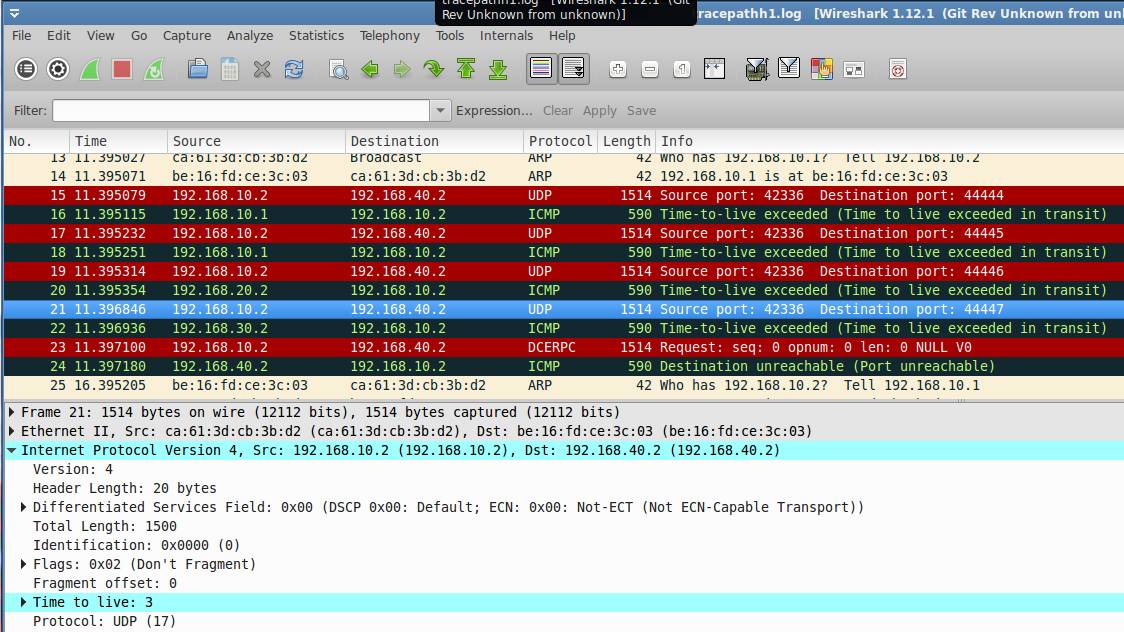
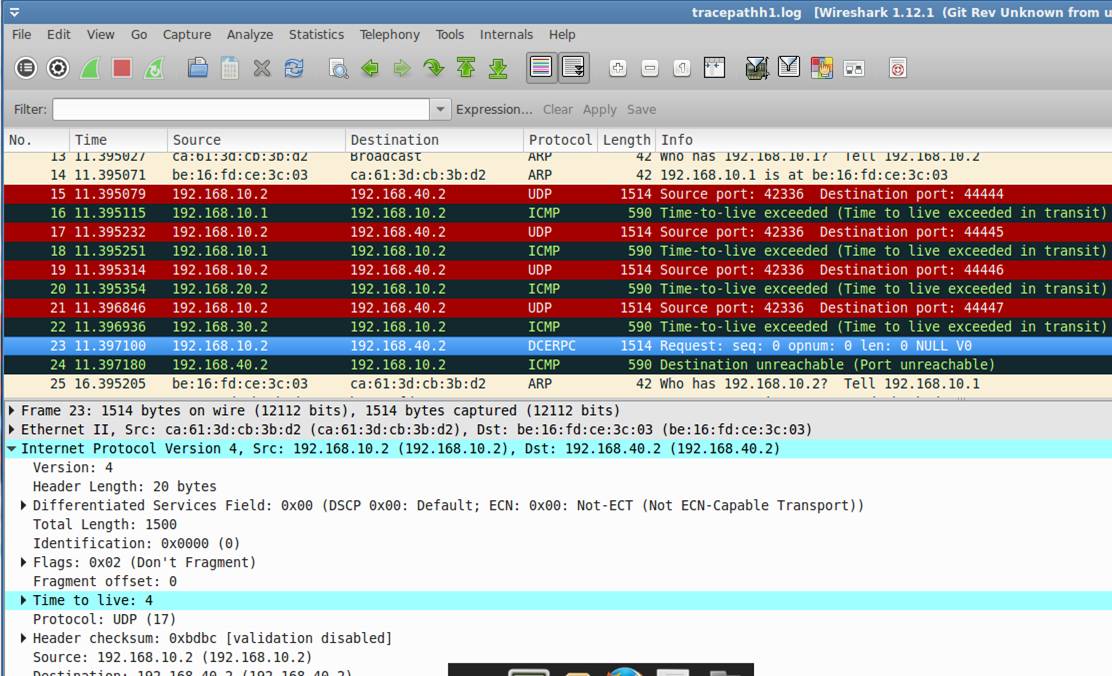
h1 and h5 are hosts while h2,h3,h4 are configured as routers. We want to use "tracepath (like tracert or traceroute)" to find the path from h1 to h5.
mininet-script
|
#!/usr/bin/env python from mininet.cli import CLI from mininet.link import Link,TCLink,Intf from mininet.net import Mininet from mininet.node import RemoteController
if '__main__' == __name__: net = Mininet(link=TCLink) #h1 is a host h1 = net.addHost('h1') #h2 is a router h2 = net.addHost('h2') #h3 is a router h3 = net.addHost('h3') #h4 is a router h4 = net.addHost('h4') #h5 is a host h5 = net.addHost('h5') Link(h1, h2) Link(h2, h3) Link(h3, h4) Link(h4, h5) net.build() h2.cmd('ifconfig h2-eth0 192.168.10.1 netmask 255.255.255.0') h2.cmd('ifconfig h2-eth1 192.168.20.1 netmask 255.255.255.0') h2.cmd("echo 1 > /proc/sys/net/ipv4/ip_forward") h2.cmd("ip route add 192.168.30.0/24 via 192.168.20.2 dev h2-eth1") h2.cmd("ip route add 192.168.40.0/24 via 192.168.20.2 dev h2-eth1") h3.cmd('ifconfig h3-eth0 192.168.20.2 netmask 255.255.255.0') h3.cmd('ifconfig h3-eth1 192.168.30.1 netmask 255.255.255.0') h3.cmd("echo 1 > /proc/sys/net/ipv4/ip_forward") h3.cmd("ip route add 192.168.10.0/24 via 192.168.20.1 dev h3-eth0") h3.cmd("ip route add 192.168.40.0/24 via 192.168.30.2 dev h3-eth1") h4.cmd('ifconfig h4-eth0 192.168.30.2 netmask 255.255.255.0') h4.cmd('ifconfig h4-eth1 192.168.40.1 netmask 255.255.255.0') h4.cmd("echo 1 > /proc/sys/net/ipv4/ip_forward") h4.cmd("ip route add 192.168.10.0/24 via 192.168.30.1 dev h4-eth0") h4.cmd("ip route add 192.168.20.0/24 via 192.168.30.1 dev h4-eth0") h1.cmd("ifconfig h1-eth0 0") h5.cmd("ifconfig h5-eth0 0") h1.cmd("ip address add 192.168.10.2/24 dev h1-eth0") h1.cmd("ip route add default via 192.168.10.1 dev h1-eth0") h5.cmd("ip address add 192.168.40.2/24 dev h5-eth0") h5.cmd("ip route add default via 192.168.40.1 dev h5-eth0") h1.cmd("tcpdump -i h1-eth0 -U -w tracepathh1.log &") CLI(net) net.stop() |
execution
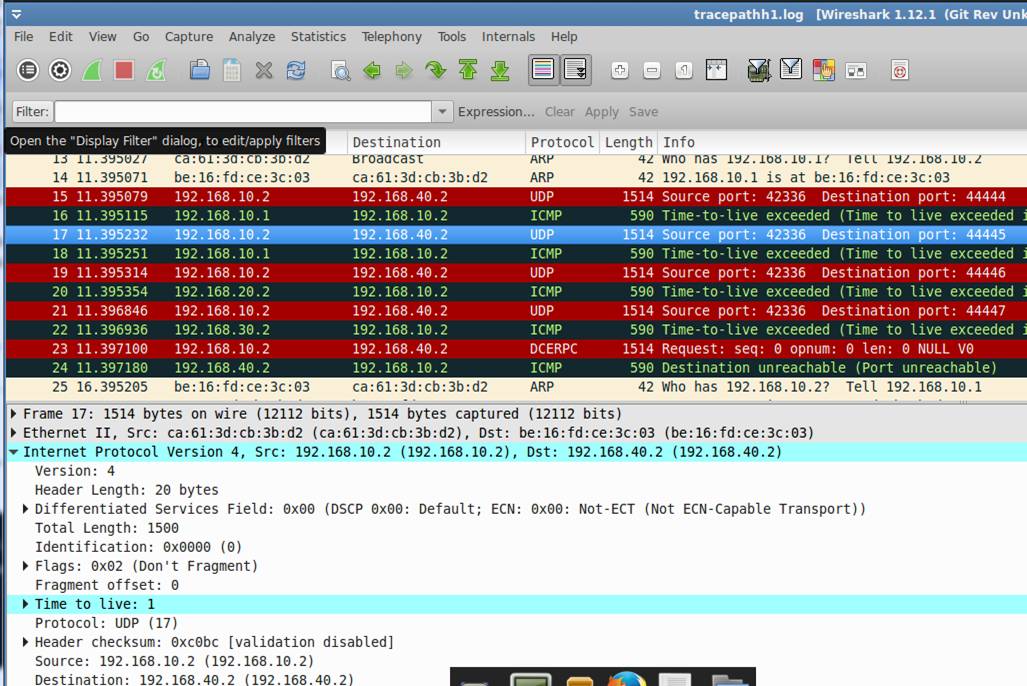
![]()
Initially, ttl is set to 1. The first router will inform the sender by ICMP packet. Then the sender will know the first router address.
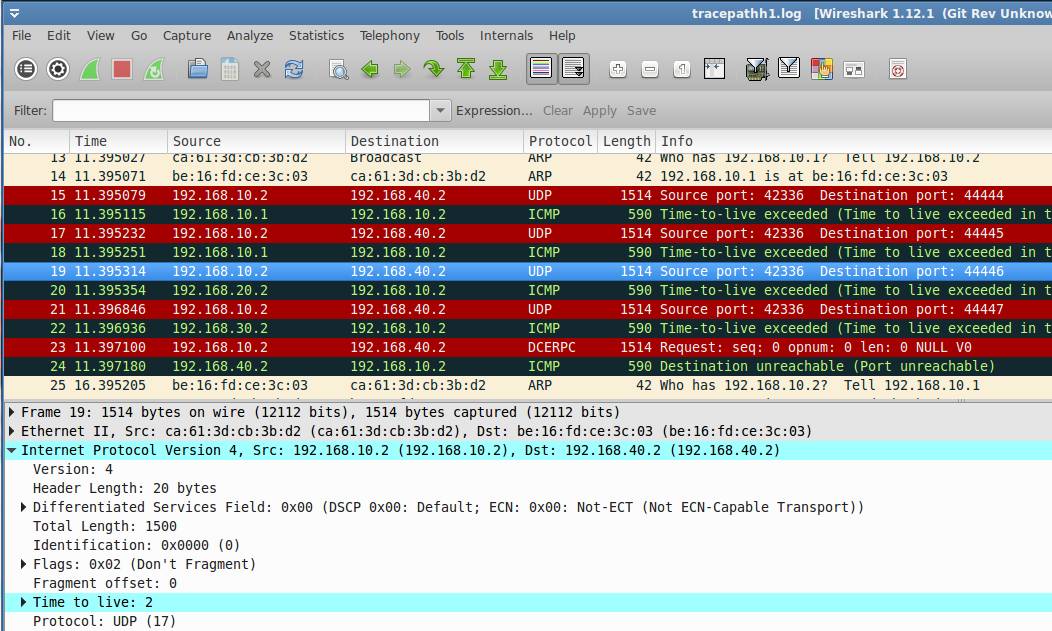
Then, the ttl is set to 2. The second router will inform the sender by ICMP packet due to TTL timeout. The sender will know the second router.
Similar results.
Dr. Chih-Heng Ke
Department of Computer Science and
Information Engineering, National Quemoy University, Kinmen,
Taiwan
Email: smallko@gmail.com